Identity theft is one of the fastest-growing crimes in the nation - especially in the suburbs, Melissa Bean
Security is a big concern for everyone. Some typical security attacks include:
-
Phishing attack. This is an attempt to steal private information, such as usernames, passwords, and credit card details.
-
Malware is short for malicious software. Some examples are viruses, worms, Trojan horses, etc. These are malicious and unwanted programs that are designed specifically to damage or disrupt computers, networks or mobile devices, gather sensitive information, or gain access to private computers.
-
Spam can be defined as electronic junk mail. It is an unsolicited email message from someone you don’t know that invites you to view pornography, purchase products and services, etc.
-
Identity theft is a crime in which someone steals your identity and gains access to your bank accounts, credit cards, etc.
-
Spyware is a combination of the words “spy” and “software”. They are programs designed to secretly monitor your activities and gather information about you and your online behavior without your knowledge or permission.
Actions you can take to be secure online
- Understand that everything you do, say, and share online (your searches and browsing history, YouTube videos you’ve watched, emails, posts, messages, and tweets you’ve written, shared, or whatever) can be tracked, stored, and distributed, it will say something about you publicly as they are likely to be available to someone who was not initially intended to or maybe everyone.
- Minimize your digital footprint: Delete web accounts, apps, email addresses, online profiles, files, etc. that you don’t really need. Every web account or app could be a potential threat. Use justdelete.me, a directory of direct links to delete your account from web services and Own Your Data, a free service to send organizations and companies a data deletion request.
Before deleting any account, you may want to spam it with random information, pictures, and videos.
- Do not give away any personal information on the Internet, especially on social networking sites and messaging services.
Never give out personal information in emails or during phone calls unless you have personally initiated the contact. Store Social Security cards, unused credit cards, checks, and personal documents in a safe place, avoid putting them in your wallet.
- Do not insult, harass, bully, or intimidate others. Do not post racist, sexist, homophobic, pornographic or generally hateful posts, comments, pictures or videos. Respect other people’s points of view and ideas, don’t be rude, mean, or abusive!
- Adjust your security or privacy settings on Facebook and other social media. Set your privacy settings to only friends.
- “Treat your online conversations as if you were talking with people in a public space where you can be seen and overheard. Don’t post or tweet under the influence of alcohol or drugs,” Peterborough Safeguarding Children Board.
- If you want to express your ideas in a forum, write a post or a comment in a blog, etc., make sure your criticisms are accurate and constructive. Don’t defame or slander anyone online.
One thing is to spread rumors or talk badly about someone with a friend in the middle of nowhere, a real private conversation, let’s say you’ve just failed an exam and obviously, you blame the teacher for not doing a good job or being incompetent. It will not make you any smarter, prettier or more successful, but this communication is private and its scope is very limited. However, writing a blog post, a comment, a tweet, etc., about him or her is a quite different beast.
What you write today, could be read years, even decades from now and it can haunt you and your teacher for the rest of your lives. It could be other people’s first impression of you and of those whom you have written about. It can affect people’s reputations, friendships, livelihoods, and well-beings, as well as having a devastating effect on your life. Besides, writing false and defamatory statements is illegal, and you can get sued for it. Think very carefully about what you are going to say before you write it online!
- “Do NOT take pictures (or videos) of yourself in any compromising position especially in various stages of getting undressed ― period. If you do take pictures (or videos) of yourself in the nude, do NOT send them to anyone ― period,” DMCA, How to stop compromising pictures of you being published online. If someone else does, ask him/her to delete it, and make sure that the photo or video has been deleted.
There have always been boys who have been able to watch naked girls in the bathroom, showers, etc. When girls are drunk, some boys have often taken advantage of this situation, too. However, seeing a friend’s breasts during a crazy party is not the same as taking a photo or video and uploading it online. In the second case, this person is damaging her reputation and well-being for her whole life.
Before uploading any content, please consider your action’ implications and don’t upload any embarrassing or private photos or videos.
- If you are being cyberbullied: don’t respond or retaliate; save the evidence, print out all abusive messages, posts, or emails; ask for help, tell an adult you trust; report it to the website, app, or social network and the police; block the person who is harassing you, change your mobile number, email address, etc.
- Create multiple emails for various purposes, so you could avoid having a unique point of failure.
- Use a good antivirus, an anti-spyware, and a firewall.
- Use VIRUSTOTAL. It analyzes suspicious files, domains, IPs and URLs to detect malware and other breaches and automatically share them with the security community.
- Do not install multiple AntiVirus programs.
- Backup your personal files and folders.
- It is very important to emphasize that they are reliable if and only if they are updated regularly so that they are able to detect and remove the latest security threats.
- Never, ever click on unverified links in emails, messages or unfamiliar websites.
- Attachments in emails and messaging can come from unreliable or unknown sources. They can contain viruses or spyware. Don’t open any attachments without first scanning them for viruses.
- Browse only ‘safe’ websites. URLVoid.com is a free service that “allows users to scan a website address with multiple website reputation engines and domain blacklists to facilitate the detection of possible dangerous websites, used to distribute malware and spyware or related to fraudulent activities.”
- Never insert unknown USB sticks or disks into your computer.
- Don’t download things you don’t know, be careful with pen drives or don’t use them at all.
- Ask yourself if you need to use P2P networks and pirate software. Many viruses and spyware use P2P sharing tools to spread everywhere. Are you sure that you cannot use free software instead? There are many free alternatives to proprietary software: GNU/Linux (operating system), OpenOffice/LibreOffice (office suite), VLC (media player), Gimp (photo editing), 7-zip (package manager), etc.
- Always keep the operating system, drivers, and all your applications updated. Set automatic updates on your device or computer.
- Shop on trustworthy web addresses starting with ‘https’, displaying the padlock icon or a green address bar that indicates the Web site is secure. Use only Amazon, Ebay or PayPal to make purchases on-line so you don’t have to trust other parties with your credit card details.
- Don’t just rely on your credit card company or bank to alert you of suspicious activity. Monitor your bank and credit card accounts regularly to ensure that no any fraud transactions is happening in your account.
- Watch what you say online, do not post or share personal information, such as your address, date of birth, telephone number, credit card number, etc. Do not answer any email or text messages that ask you for confidential information, such as your bank account, name, Social Security number, passwords, etc. even if it appears to be from Google, your bank, or a relative.
- Shred documents containing personal and sensitive information, e.g., pre-approved credit card applications, canceled or unused checks, old bank statements, ATM receipts, or obsolete ID cards (expired driver’s licenses, medical insurance cards, and passports).
- Do not answer any email saying you have won or inherited a large amount of money and that you need to pay a fee or provide your banking details or other information to access or receive the money.
Be wary of offers that seem too good to be true, “advance fee schemes" (they will contact you by email, letter, text message or through social media, and ask you to pay money to someone in anticipation of receiving a gift, a contract, a lottery price, or a large inheritance), and emails that appear to be from friends and include a generic subject line, such as I love you, you really need to see this, you need to see these pictures/videos. They can steal your address book and send malware emails to every address on it.
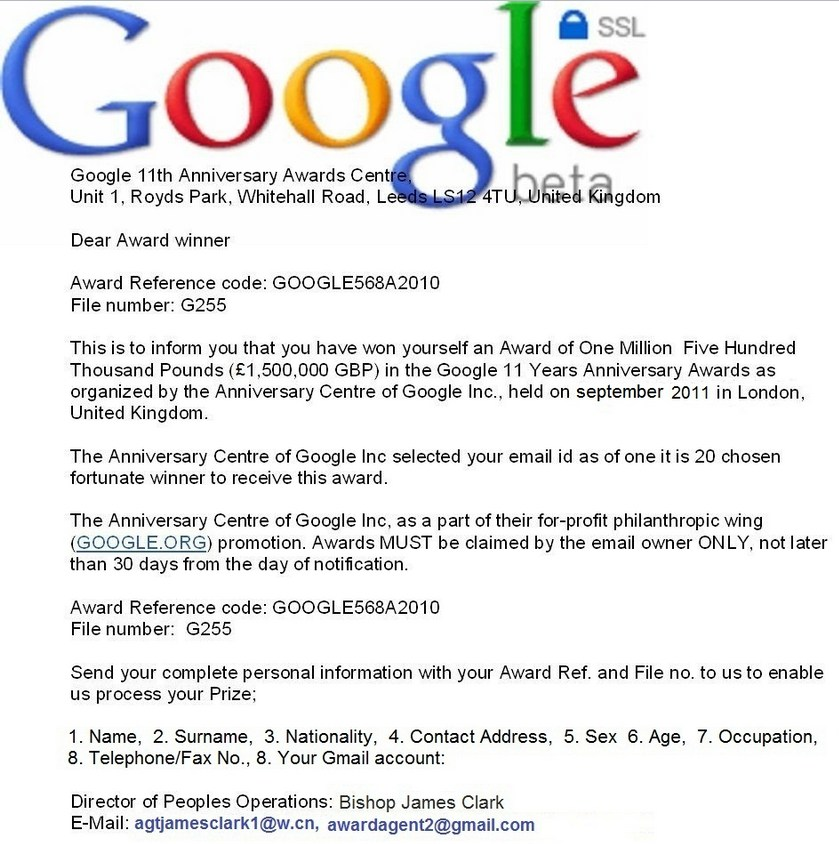
You can also use Google to know more about the scam.
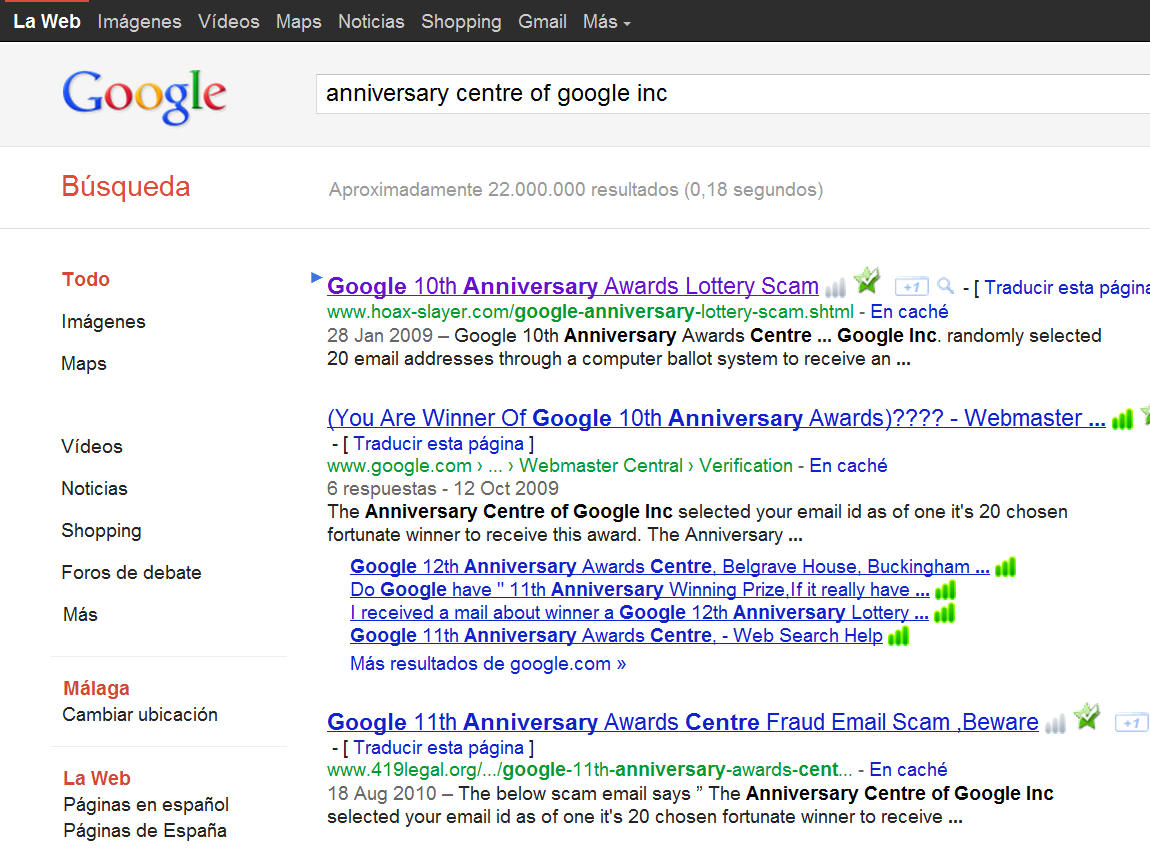
If it’s too good to be true, then it probably is a scam.