
|
 |
 |
|
 |
Identity theft is one of the fastest-growing crimes in the nation ― especially in the suburbs, Melissa Bean.
Identity theft is a form of stealing someone's identity in which someone pretends to be someone else by obtaining his or her personal or financial information, such as bank account number, credit card information, driver’s license, Social Security number, etc., and assuming that new identity to use it to commit fraud, such as making unauthorized transactions or purchases, obtaining free medical care, or conducting criminal activity (tax evasion, illegal immigration, etc.)
It is a traumatic and difficult experience and their victims are left with bills that they did not incur, damage to their credit, finances, and reputation.
Children and the elderly are particularly vulnerable. Thieves obtain personally identifiable information by many means: hacking computer networks, information leakage, social engineering, brute-force attacking weak passwords, using malware, such as spyware, Trojan horses or keystroke logging programs, etc.
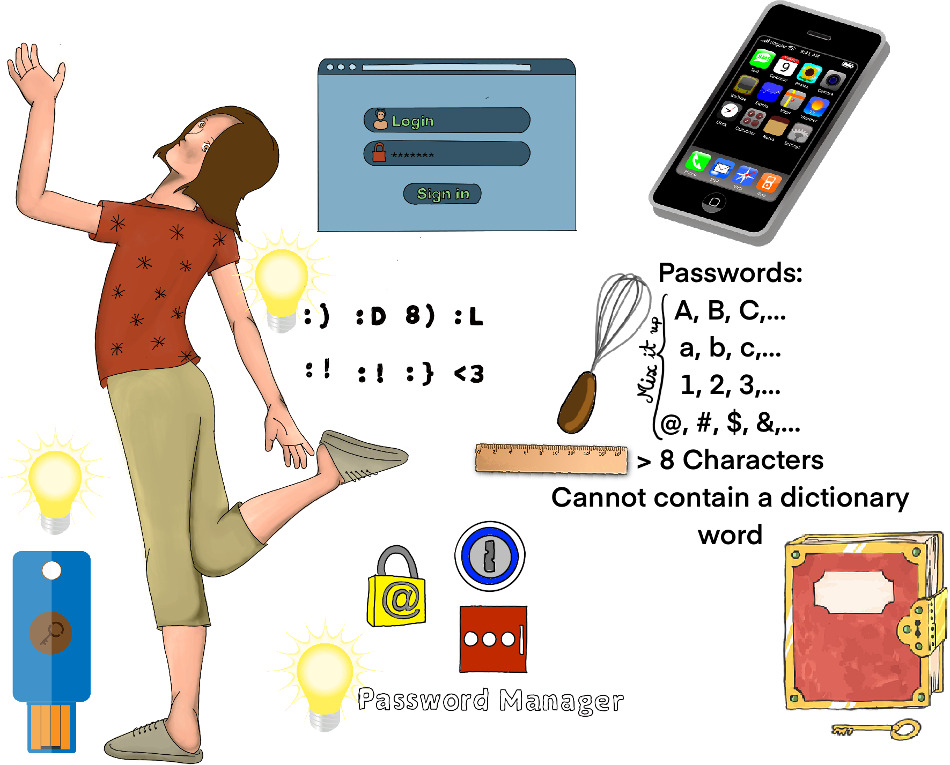
33% of citizens in the US and 40% consumers worldwide have experienced identity theft at some point in their lives. Every year, 15 million Americans become victims of identity theft.
The situation looks dark and gloomy. Deepfakes, left unchecked, are set to become the cybercriminals’ next big weapon.