Privacy is one of the biggest problems in this new electronic age, Andy Grove
Privacy is an inherent human right, and a requirement for maintaining the human condition with dignity and respect, Bruce Schneier
Hell is empty and all the devils are here, William Shakespeare.
We are living in difficult and distressing times, there is no doubt about it. Privacy is both a human right and a necessity, and big companies, tech titans, governments, small companies, and hackers are constantly attacking and diminishing our privacy. The loss of privacy has a corrosive and perversive effect on all of us, both as individuals and society as a whole.
For Orwell, Huxley, Bradbury, Atwood and many others, it was one of the establishing nightmares of the totalitarian future. It is the regression towards an uncivilized society, devoid of freedom and where there is a widespread use by the ruling elite of the threat of aggression as a means of controlling the masses and ensuring compliance.

We all deserve and need to have privacy oline. This is a follow-up article to a previous one about how to browse anonymously. It is very important to take back control of your data, be safe online, and improve your privacy and security on the Internet. Regain your digital privacy.
Tails is a portable operating system that protects you against surveillance and censorship. It uses the Tor network to protect your privacy online and help you avoid censorship.
MAC address anonymization is enabled by default for all network interfaces. Besides, Tails comes with the Tor Browser to browse the web anonymously and uncensored; Thunderbird, an email client; KeePassXC, a password manager; and Pidgin Internet Messenger. Tails does not ship with any torrent client software and is unlikely to do so in the future because Tor with BitTorrent is not secure and is a threat to your online anonymity.
Tails, aka the Amnesic Incognito Live System, is a stateless operating system focused on privacy, and it should be used for some specific activities, such as reporting abuse or corruption, serious and sensitive business activities, publishing anonymous posts, etc., that need to be kept anonymous, and nothing else.
How to install and use it.
- Create a bootable USB using Rufus, balenaEtcher, or Ventoy.
- Go to Tails and download the latest ISO. If you are using Ventoy, you just need to copy the ISO image to your USB stick.
- Set up your computer to boot from your USB flash drive.
- Boot from your USB with Tails, configure and start Tails. First, you need to configure your language and keyboard layout. You can add a custom setting (e.g., an Administration Password) by pressing the plus “+” button in the left corner. Finally, click on the Start Tails button.

- There are two options to connect to the Tor network: Connect to Tor automatically, this is the easiest and fastest option. It uses a public relay as your first Tor relay, and by doing so, it makes it clear to your local network that you are connecting to Tor, while still keeping your online activity secure and anonymous. If connecting to Tor is blocked in your country or looks suspicious to someone who monitors your Internet connection, use the second option, Hide to my local network that I’m connecting to Tor. It uses tor bridges, i.e., secret Tor relays that keep your connection to the Tor network hidden. When you are done, smash the Connect to Tor button, then Start Tor Browser.
To connect to a WiFi network, open the settings menu in the top-right corner, choose Wi-Fi Not Connected, select Network, and then choose the correct Wi-Fi network.
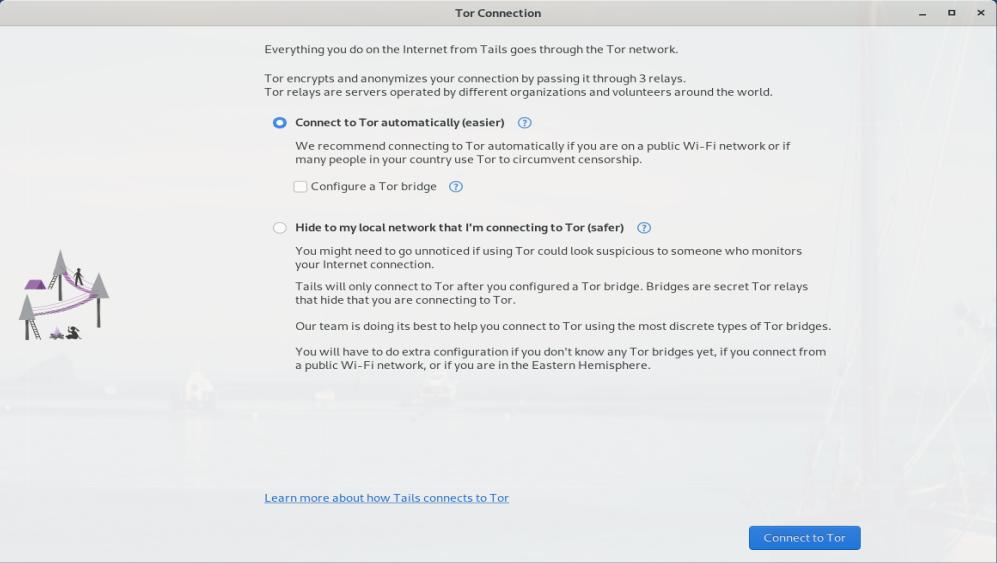
- Click on Tor Check to verify that you are actually connected to the Tor network.
Onion or hidden services are those that are only accessible through the Tor network. An onion address is a string of 56 letters and numbers, followed by “.onion”. They are hidden from public view and search engines (Google, Yahoo, Bing), and all traffic between Tor users and these services is end-to-end encrypted.
Go to Tor Browser’s Settings, Privacy, you should set Onion Services. Prioritize .onion sites to Always and set Security Level to Safest.

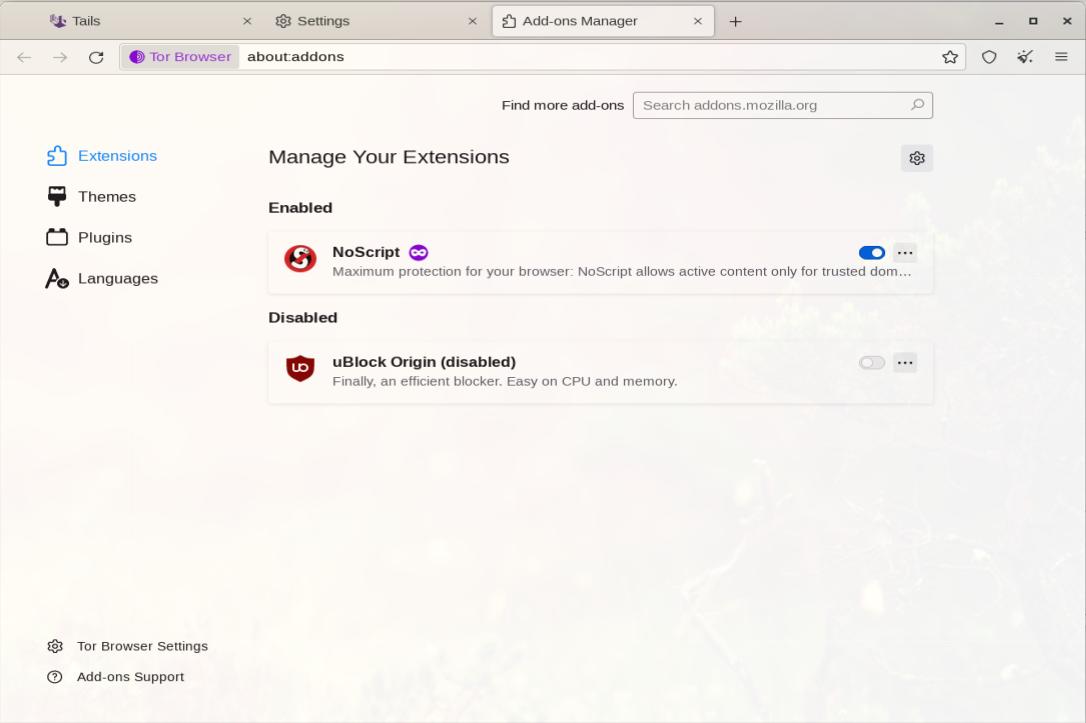
- Tor Browser already comes installed with one add-on — NoScript — and adding anything else could deanonymize you, so installing new add-on extensions like AdBlock Plus or uBlock Origin is strongly discouraged. Therefore, go to Settings, Extensions and Themes, and disable uBlock Origin.
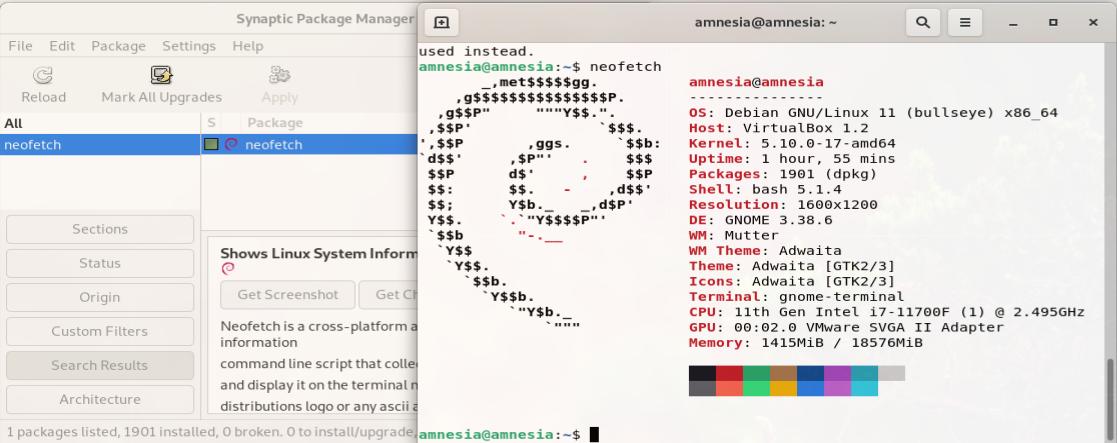
- To install additional software: set up an administration password when you start Tails; Launch Synaptic (Applications, System Tools, Synaptic Package Manager), search for the name of the package that you are interested in (e.g., neofetch), right click on the name of the package, and select the Mark for Installation option from the contextual menu, then Apply.
- It is obvious, but it is worth saying, always keep your system up-to-date .
- Tor anonymizes the origin of your network traffic and encrypts everything inside the Tor network, but it does not encrypt your Internet traffic outside the network. Do not use HTTP websites, but surf through HTTPS websites, and use add-ons like HTTPS Everywhere.
- Everything you save inside Tails will be deleted and gone after you finish the session. However, you have the option to save personal files, additional software, and some settings in the Persistent Storage. Everything in the persistent storage will remain available across different sessions and will be encrypted using a passphrase!
A. To create the persistent storage, select Application, Tails, Configure persistent volume. Type in a passphrase and click on the Create Button.
B. Turn on some features of the Persistent Storage. Each feature corresponds to a set of files or settings that can be saved in the Persistent Storage.
C. Restart. In the Welcome to Tails! screen, in the Encrypted Persistent Storage section, enter your passphrase, and click Unlock to unlock the persistent storage for the current session.
Alternatives
- Qubes OS is one of the most secure operating systems out there. It is an alternative to Tails.
- Whonix runs like an app inside your operating system - keeping you safe and anonymous. It is more convenient than Tails because you do not need to restart your computer to use it.








