Privacy is one of the biggest problems in this new electronic age, Andy Grove
Privacy is an inherent human right, and a requirement for maintaining the human condition with dignity and respect, Bruce Schneier
We are living in difficult and distressing times, there is no doubt about it. Privacy is both a human right and a necessity, and big companies, tech titans, governments, small companies, and hackers are constantly attacking and diminishing our privacy. It has a corrosive and perversive effect on all of us, both as individuals and society as a whole.

You deserve and need to have privacy oline. Read this article to take back control of your data, be safe online, and improve your privacy and security on the Internet. Regain your digital privacy.
- Use a VPN. A VPN protects your privacy. It separates your location from your data. It is basically a secure tunnel between you and the Internet, so all your traffic is encrypted.
- To stay anonymous, you can browse from a public Wi-Fi access point, so your connection to the Internet do not involve your ISP (Internet Service Provider).
- Do not use Windows or macOS as your operating system and, even worse, a Microsoft account as your login. Create a local account instead.
- Use Tor. It is a web browser that lets users stay anonymous online and protects them from being tracked by hackers, internet service providers, and even corporations and governments.
- If you don’t want to use Tor, do not use Google Chrome and install privacy-protecting extensions such as HTTPS Everywhere (it encrypts your communication with many major websites), Privacy Badger (it stops advertisers and other third-party trackers from secretly tracking where you go and what pages you visit/look at on the web), Ghostery (it blocks adds and stops third-parting tracking cookies); and NoScript (it allows Javascript and other potentially harmful content to be executed only by trusted web sites of your choice, e.g., your online bank).
- Spoof your MAC address.
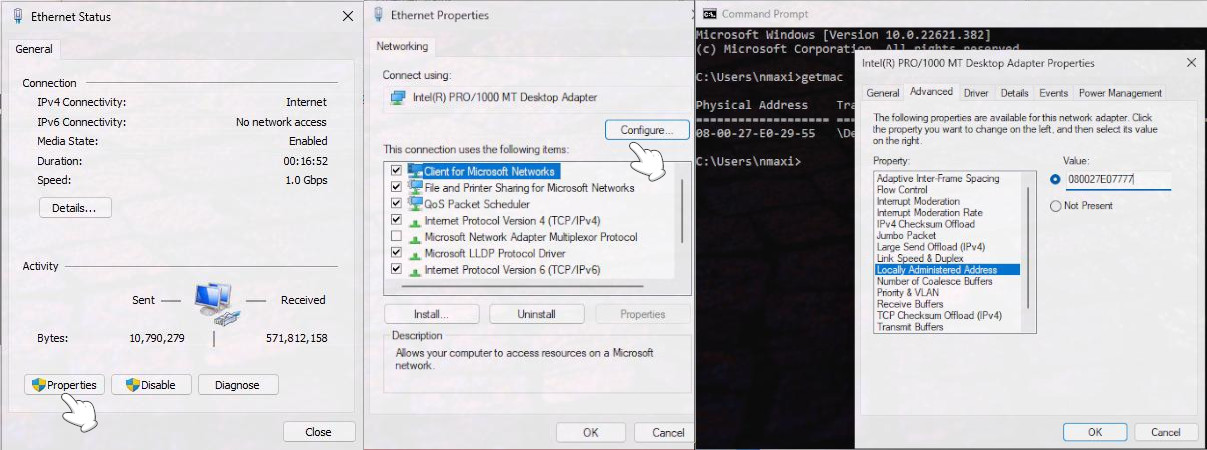
- Windows: Start, Control Panel, Network and Internet, Network and Sharing Center, Change adapter settings. Click on Local Area Connection/Ethernet, then on Properties and Configure. Switch to the Advanced tab, click on the Locally Administered Address property, tap on the Value checkbox, and type in a new MAC Address.
Before and after changing your MAC address, check your current MAC Address by entering CMD in the Start menu search bar, then typing in Getmac.
- macOS: Open a terminal and type: ifconfig en0 | grep ether to verify the existing MAC address. Change your MAC Address: ifconfig en0 ether 9c:47:5e:59:68:7c, and confirm that your MAC Address has been changed. If you need to protect your privacy at all costs, WifiSpoof is a pricey app that provides a way to randomize your new MAC address every few minutes.
- GNU/Linux: sudo pacman -S macchanger (it installs the manchanger package); sudo ifconfig eth0 down (it deactivates eth0); sudo macchanger eth0 -r (it spoofs the MAC address of the eth0 interface with a fully random address); sudo ifconfig eth0 up (it activates eth0).
However, we want to spoof our MAC address automatically:
user@pc:~$ ip link show # It lists all interfaces
1: lo: mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
2: enp5s0: mtu 1500 qdisc fq_codel state UP mode DEFAULT group default qlen 1000
link/ether 7c:10:c9:42:f2:b7 brd ff:ff:ff:ff:ff:ff
3: wlo1: mtu 1500 qdisc noqueue state DOWN mode DORMANT group default qlen 1000
link/ether 9a:1e:5f:9d:5f:77 brd ff:ff:ff:ff:ff:ff permaddr 14:85:7f:b9:6f:b8
altname wlp0s20f3
sudo ip link set wlo1 down && sudo ip link set enp5s0 down # It deactivates all interfaces.
touch /etc/systemd/system/macspoof@.service # Let's create a service:
[Unit]
Description=macchanger on %I
Wants=network-pre.target
Before=network-pre.target
BindsTo=sys-subsystem-net-devices-%i.device
After=sys-subsystem-net-devices-%i.device
[Service]
ExecStart=/usr/bin/macchanger -r %I
This is the key line. It spoofs the MAC address of the interface with a fully random address.
Type=oneshot
[Install]
WantedBy=multi-user.target
systemctl enable --now macspoof@enp5s0.service && systemctl enable --now macspoof@wlo1.service # Let's enable the service for both interfaces immediately and also with every reboot
sudo ip link set wlo1 up && sudo ip link set enp5s0 up # Next, we bring back both interfaces.
if link show # Check that our MAC addresses have been changed.
- Do not use Google Chrome, but Tor, LibreWolf, or Brave; do not use Google, Bing or Yandex as search engines, but Startpage, DuckDuckGo, or searX; do not login to any online service that identifies you as you (Gmail, Microsoft, Twiter, Facebook, and so on); do not use email services such as Gmail, Hotmail, or Yahoo Mail, but a throwaway or temporary email, such as 10 minute Mail, Temp Mail and GuerrillaMail, or a privacy friendly email provider, e.g., ProtonMail, Tutanova, Librem Mail, Mailfence, etc. Be minimalist, the fewer applications, data, and resources you have, a safer, more private and results-oriented environment you have.
- Use Tails, a portable operating system that protects you against surveillance and censorship. It uses the Tor network to protect your privacy online and help you avoid censorship. Shut down your computer and start on your Tails USB stick, so Tails will leave no trace on the computer when you shut it down after using it.
Are you becoming increasingly paranoid? Then you should use GNU/Linux (Tails), spoof your IP and MAC address, connect to a public Wi-Fi access point, and then browse exclusively through TOR.
- Another idea is to route all your system traffic through tor. Tor is a free, volunteer-run network of virtual tunnels designed to conceal your identity, location, and online activity from tracking or surveillance.
GhostNET
GhostNET helps you be safer on the cyber network. It was made for transparently routing through tor, and of course, your network traffic will run exclusively under tor.
git clone https://github.com/t7hm1/GhostNET.git && sudo cp GhostNET/ghostnet /usr/bin/ghostnet # Let's clone its repository.
sudo cp GhostNET/ghostnet.log /opt/
sudo chown (your user name):users /opt/ghostnet.log
sudo chmod +x /usr/bin/ghostnet
sudo ghostnet # Finally, let's start it. Make sure that it works, https://check.torproject.org/.
ghostnet [start | stop | status]
Anonsurf
Anonsurf or kali-anonstealth is a tool that will anonymize your entire system under TOR using IPTables. It will basically route every packet through a TOR relay, i.e., all your traffic goes through a TOR proxy server.
- Installation (Debian, Ubuntu)
mkdir Anonsurf && cd Anonsurf
git clone https://github.com/Und3rf10w/kali-anonsurf.git # Let's clone Anonsurf
cd kali-anonsurf # Then, go to the recently downloaded folder.
sudo ./installer.sh # Next, we need to run the installer script that makes things extremely easy.
sudo anonsurf # Finally, let's start it.
anonsurf [start | stop | status]
# Start system-wide anonymous | Reset original iptables settings and return to clear navigation | Check if AnonSurf is working properly





