Password managers are used to keep all your passwords safe. They store and manage all your passwords, so you don’t need to try to memorize a bunch of unique, complex passwords for all of your personal and work accounts. You only need to remember one password, the one to your password manager. They can generate complex passwords for you. You can also set your password manager to log in to sites automatically.
There are many password managers and not all password managers are created equal:
- LastPass is a clouded-based user-friendly password manager. However, it is not free.
- KeePass is a free, open source, light-weight, and easy-to-use password manager.
- Pass is a simple, lightweight, command-line password manager built with the Unix philosophy in mind.
Virtual keyboards may be used in some cases to reduce the risk of keystroke logging. Keystroke logging is the act of recording key presses on a keyboard.
LastPass
- Create a strong master password.
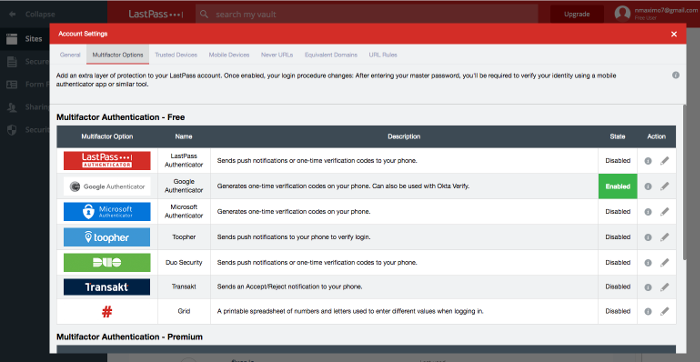
- Set up SMS Account Recovery and multifactor authentication. Open your LastPass Vault. Account Settings.
2.1 SMS Account Recovery.
2.2 Multifactor Options (LastPass Authenticator, Google Authenticator, Microsoft Authenticator, etc.).
- Restrict LastPass Access to Specific Countries: Account Setting, Show Advanced Settings, Only allow login from selected countries.
- Store Secure Notes (templates): Driver’s License, Wi-Fi passwords, credit card numbers, social security cards, passports, etc.
- Form Fills. LastPass can remember and fill in name, birth date, gender, mailing address, email address, phone number, credit card information, social security number, etc.
Pass
Pass is a simple, lightweight, command-line password manager built with the Unix philosophy in mind. It keeps passwords inside gpg2 encrypted files inside a tree residing at ~/.password-store. It maybe the only free password manager you’ll need.

If you don’t like the terminal, QtPass is a multi-platform GUI for pass.
- Please select what kind of key you want: (1) RSA and RSA (default)
- What key size do you want? (3072 or 4096)
- Please specify how long the key should be valid. 0 = key does not expire.
- Name and email address.
- A secure passphrase.
- List our current active keys: gpg ‐‐list-secret-keys ‐‐keyid-format LONG and copy the ID of your Key, aka KEY_ID.
> gpg --list-secret-keys --keyid-format LONG
~/.gnupg/pubring.kbx
---------------------------------
sec rsa3072/YOUR_KEY_ID 2022-05-17 [SC]
04FA2365C1C45DA77CC34611YOUR_KEY_ID
uid [ultimate] YourName <YourEmail>
ssb rsa3072/D8E947D170DF786E 2022-05-17 [E]
- Initialize a password store: pass init YouEmail or pass init “KEY_ID”.
- Add passwords: pass insert amazon.com. It is saved in .password-store/amazon.com.gpg and it can be decrypted with gpg -d amazom.com.gpg. pass insert SocialNetworks/myTwitterUser
- To get a view of the password store: pass
- Retrieve a password: pass amazon.com, pass SocialNetworks/myTwitterUser copy it to the system’s clipboard, pass -c amazom.com.
- To generate a new random password: pass generate SocialNetworks/myFacebookUser n, where n is the desired password length, e.g., n = 12
- You can remove passwords (pass rm pass-name) or edit them (pass edit pass-name). This is ideal when you need to store additional security details, such as two-factor authentication recovery codes, login details, etc.
- You can use pass for two factor authentication,p too:
user@pc:~$ pacman -S zbar pass-otp # ZBar Bar Code Reader is an open source software suite for reading bar codes
user@pc:~$ zbarimg -q GoogleQR.png # It scans a QR code using the zbarimg command.
QR-Code:otpauth://totp/ServiceName%3userName%40gmail.com?secret=XXXXXXXXXXXXXXXXXXXXXX&issuer=ServiceName # The URL starts with otpauth://totp/, which indicates it’s related to two-factor authentication (2FA) using time-based one-time passwords (TOTP).
user@pc:~$ pass otp add googleotp # Add an OTP entry named googleotp
Enter otpauth:// URI for googleotp: otpauth://totp/ServiceName%3userName%40gmail.com?secret=XXXXXXXXXXXXXXXXXXXXXX&issuer=ServiceName # You're prompted to enter the outpauth:// URI for this entry, which matches the decoded QR code data.
Retype otpauth:// URI for googleotp: otpauth://totp/ServiceName%3userName%40gmail.com?secret=XXXXXXXXXXXXXXXXXXXXXX&issuer=ServiceName
user@pc:~$ pass otp googleotp # Retrieve the OTP for googleotp. The OTP generated by your authenticator app (such as Google Authenticator) will match the one you’ve retrieved using pass otp googleotp.
123456
- Search for passwords: (find/grep)
> pass find amazon
Search Terms: amazon
└── Root
├── Ocio
│ └── amazon.es
- Migration to pass. Use pass-import, a pass extension for importing data from most of the existing password manager.
- It is available in the Arch User Repository: yay -S pass-import
- Migration from KeePassXC. Export the database to CSV. Launch KeePassXC: Database, Export to CSV File
- pass import keepassxc /path_database/database.csv
- rofi-pass is a bash script to handle simple password store in a convenient way using Rofi. Installation: sudo pacman -S rofi-pass.
bindsym $mod+Shift+y exec rofi-pass
- Export/import private keys:
gpg --export-secret-keys <KEY_ID> > my_private_key.asc
gpg --import my_private_key.asc
- Using PAM to unlock pass. It allows to automatically unlock your GNUPG keys on login to seamlessly use pass.
- Install pam-gnup: yay -S pam-gnupg-git.
- Open the PAM configuration file for your login manager (e.g., lightdm, gdm, sddm) located in /etc/pam.d/, e.g., sudo vim /etc/pam.d/lightdm, and add the following line to the end of the file:
[···]
auth optional pam_gnupg.so store-only
# It specifies that the pam-gnupg module should be invoked during the authentication process. It allows gpg-agent to unlock your GnuPG keys using your login password.
session optional pam_gnupg.so
# It specifies that the pam-gnupg module should be invoked during the session setup.
- Configure pam-gnup: vim ~/.gnupg/gpg-agent.conf and add:
default-cache-ttl 3600 # This line sets the default cache time-to-live (TTL) for cached passphrases to 3600 seconds (1 hour). Once you enter your passphrase to unlock your GPG key, it will be cached by gpg-agent for this duration before it expires and requires you to re-enter the passphrase.
max-cache-ttl 86400 # Set max-cache-ttl 86400 to expire after a day.
allow-preset-passphrase
- Run the following command:
user@pc:~$ gpg -K --with-keygrip # Run the following command to get the keygrip for the encryption subkey
sec ed25519 2024-04-09 [SC]
A4E6D6E7387899BDDDDDD8E8F0FEB0
Keygrip = 0D14202636454856616189A690F25D
uid [ultimate] Máximo Núñez Alarcón
ssb cv25519 2024-04-09 [E]
Keygrip = 01203A3A0E425658626B70898FE4E9E9F0F19B
- These keygrips represent unique identifiers for your keys.. Write the keygrip for the encryption subkey marked [E] – shown in boldface in the output above into ~/.pam_environment:
PAM_GNUPG_KEYGRIPS=YOUR_KEYGRIP_HERE
- Edit $XDG_CONFIG_HOME/pam-gnupg/keygrips and add your keygrips:
Trouble shooting: The XDG_CONFIG_HOME environment variable plays a crucial role in determining where user-specific configuration files should be stored. Edit ~/.bashrc or ~/.zshrc and add: ~/.bashrc or ~/.zshrc. Create Configuration Directory for pam-gnupg: mkdir -p $XDG_CONFIG_HOME/pam-gnupg.
If you want convenience (sacrifice security💣) sudo visudo: mysuser ALL=(ALL) NOPASSWD: ALL, it grants mysuser privileges on all hosts, allowing them to run any command as any user or group and he would not be prompted for a password when using sudo.
- Sync with a Git repo so you can share your passwords and credentials across multiple devices.
-
Create a private repository. Create a new repository. Repository name: pass. Visibility level: Private.
-
Initialize it locally: pass git init
-
Add the remote origin:
pass git remote add origin https://github.com/nmaximo7/pass.git
-
Push your pass store to the remote repository: pass git push -u –all. Username: yourUserName. Password: yourPersonalAccessToken. You need to have or create a personal access token (PAT).
- Install BrowserPass - native messaging host, it is a host application for browserpass browser extension providing it access to your password store, sudo pacman -S browserpass
- You also need Browserpass - browser extension, a browser extension for pass.
-
Biography: Guia completa pass, lignux.com, Arch wiki, pass
-
Visudo. It is a command-line utility that allows editing the sudo configuration file in a fail-safe manner. You can add a line to allow your user to run any command without a password: yourusername ALL=(ALL) NOPASSWD: ALL
KeePassXC
KeePassXC is a free cross-platform password manager.
- Installation. KeePassXC. macOS: brew install ‐‐cask keepassxc. Debian, Ubuntu: sudo apt install keepassxc. Arch: sudo pacman -S keepassxc
- Export LastPass Vault’s data. A. Using Firefox, go to LastPass: Advanced, Export, LastPass CSV File and save it as a CSV file. B Import it in KeePassXC: Database, Import, CSV File. Database Name: Passwords. Save it (Passwords.kdbx) in Google Drive/Dropbox/etc. Import CSV Fields. Check column association (Username: Column3, Password: Column 4, URL: Column 5, etc. it may vary).
- Use it in your favorite browser. Launch KeePassXC, select the Settings option or the cog wheel icon from the Tools menu, and then, Browser Integration, Enable browser integration. In the General tab: Enable integration for these browsers: Chrome, Firefox, Brave, etc. Open your browser, install the extension KeePassXC-Browser, and connect it to KeePassXC. Give the connection a unique name, then click on Save and allow access.
- Use KeePassXC in your phone, too. Install the Keepass2Android Password Safe app. Open file…, Google Drive/Dropbox/etc., Select Passwords.kdbx, Type your Master Key.
- Set up 2FA TOP with KeepassXC. Right-click on any entry, TOTP, Set up TOTP and copy the TOTP code, e.g., Twitter: More, Settings and privacy, Security, Two-factor authentication, Check authentication app, Can’t scan QR code. To view it, right-click on the entry, TOTP, Show TOTP. To transfer it to Google Authenticator. Select the entry that contains the secret key, TOTP, Show QR Code.
You can always use a QR scanner app or zbar. ZBar is an open source software suite for reading bar codes from various sources.
sudo pacman -S zbar # 1. Install the zbar package (Arch). sudo apt-get install zbar-tools (Ubuntu, Debian, or similar)
zbarimg $ ~/codigoqr.png # 2. Decode the QR code
You will get something like:
QR-Code:otpauth://totp/Google%3Anmaximo7%40gmail.com?secret=THIS-IS-YOUR-TOTP-CODE&issuer=Google





